Over the past few years, following the growth of communication networks, internet as the biggest has been widespread popular. Using anonymity provided by the internet, hustlers set out to deceive people with false offers and make themselves look legitimate in this medium [1]. Today, financial crimes are transformed from direct attacks into indirect attacks. phishing is a kind of electronic identity theft in which a combination of social engineering and fake website creating methods is used to deceive user to disclose his/her confidential and invaluable details [2].
With increased terminals for access to information, online banking creates the need for using reliable methods in order to control and use confidential and vital information. To date, different approaches have been provided for detecting such attacks, but most of them can't detect such attacks accuracy.
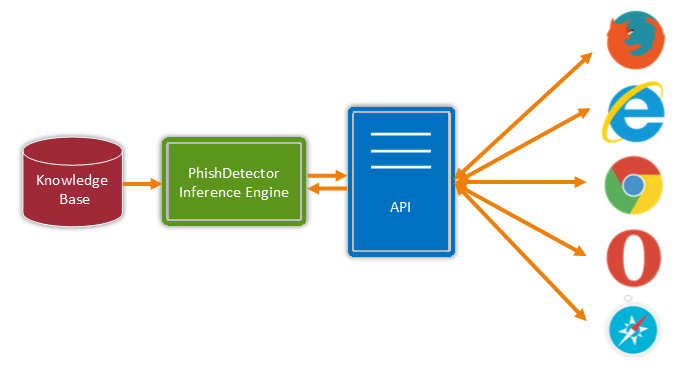
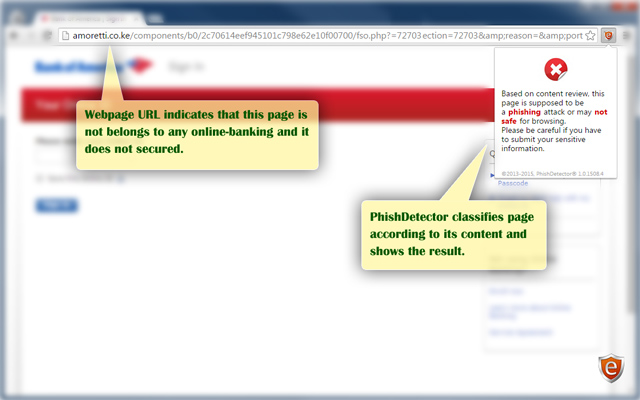
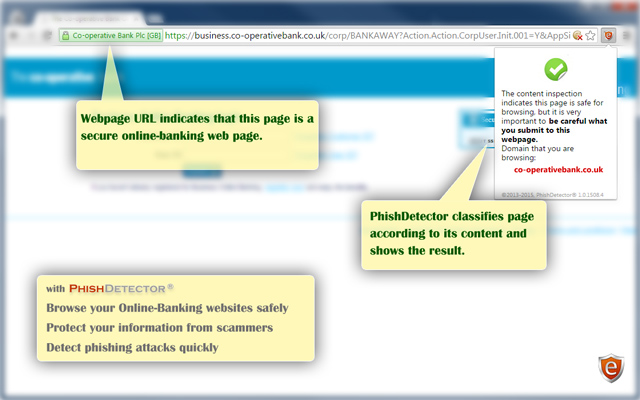
We present a new rule-based method for detecting phishing attacks in online banking by classifying web pages into Phishing and Legitimate. Our method performs the web page classification by employing the main characteristics that distinguishing the fake websites from a legitimate. Our new technique has implemented in the form of an extension for chrome browser.
Our method has more functionality such as :
- High accuracy
- Low false alarm
- Fast phishing detection
- Easy to use
- Easy customization
- ...